Fraud and security, Products
What is a one-time password (OTP)? Features and benefits explained

In a world where fraud is all too common, wouldn’t it be great to have a simple way to know you’re talking to the right person? As more of our lives happen online, the need for easy and reliable identity verification is more important than ever.
One-time passwords (OTPs), also known as one-time passcodes or a one-time PIN, add a layer of security to verify and protect users worldwide. With mobile security in high demand, the global multi-factor authentication (MFA) market is projected to be valued at $34.8 billion by 2028, as compared to $15.2 billion in 2023.
OTPs are a straightforward, cost-effective solution for organizations to verify and protect their customers’ and employees’ personal information. If you want to learn how to instantly verify your customers from anywhere in the world while saving time and money, this guide is for you.
Alejandro Murcia, Director of Financial Services at Sinch, explains how businesses can use OTPs
What is a one-time password (OTP)?
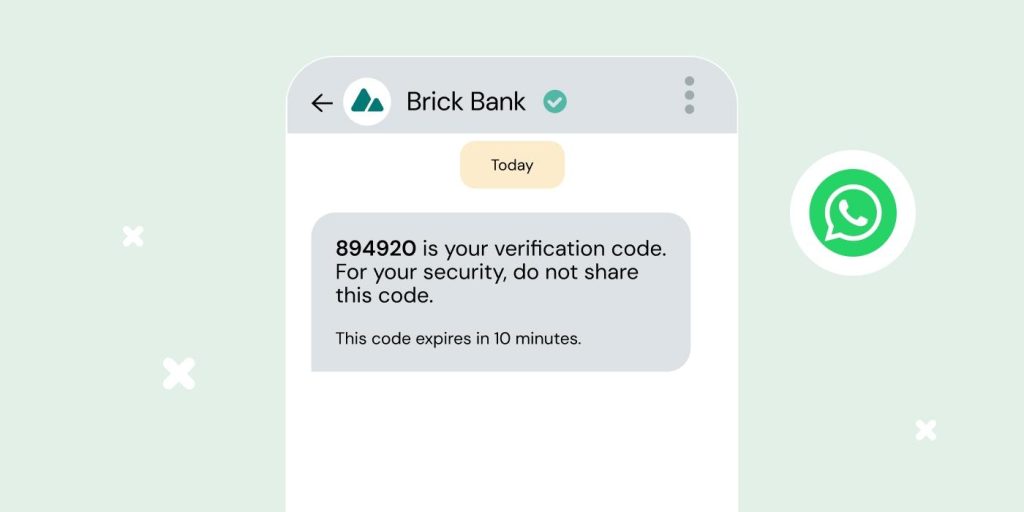
A one-time password (OTP) is a quick way to verify a user’s identity when they’re logging into an account, network, or system. The user receives a unique code – usually a string of numbers or letters – that expires after a short period of time and they can’t reuse.

OTPs can be sent to a user by email, phone call, authenticator app (common ones include Google Authenticator or Microsoft Authenticator), text message, as an RCS OTP or via another mobile messaging channel like WhatsApp, or as a push notification. They can be used as single-factor authentication to replace static passwords with a unique PIN for each session instead of requiring a username and password.
Alternatively, they can be combined with user-generated credentials for two-factor authentication (2FA), requiring both something a person knows (like a PIN) and something they have (like a key fob). This can come into play during sign-up, login, or transaction approvals, where:
- A customer attempts to use their username and password from an unrecognized device
- The customer then receives and uses their OTP to verify their identity and device
How does a user get a one-time password?
Getting an OTP is quick and easy for the end user. Here’s a common scenario:
- A customer tries to log in to their online bank from a new device.
- The bank doesn’t recognize their device. They offer to send a verification code via WhatsApp, SMS, phone call, push notification, or email.
- The customer chooses how to receive the OTP and gets it in seconds.
- The user enters the OTP along with their login details and – voila! They’re in.
Pretty cool, right? Behind the scenes, all kinds of magic happened to generate and deliver that one-time passcode to the customer. We’ll reveal the magician’s secrets in the section below.
How does a one-time password work?
Whenever a user tries to access a system or perform a transaction on an unauthenticated device, an OTP generator and an authentication server work together using security tokens (or shared secrets) to verify their identity.
First, the OTP generator uses a hashed message authentication code (HMAC) algorithm to create a new, random code for each access request.
As the name implies, all OTPs only work once, but the unique password will either be hash-based (HOTP) or time-based (TOTP).
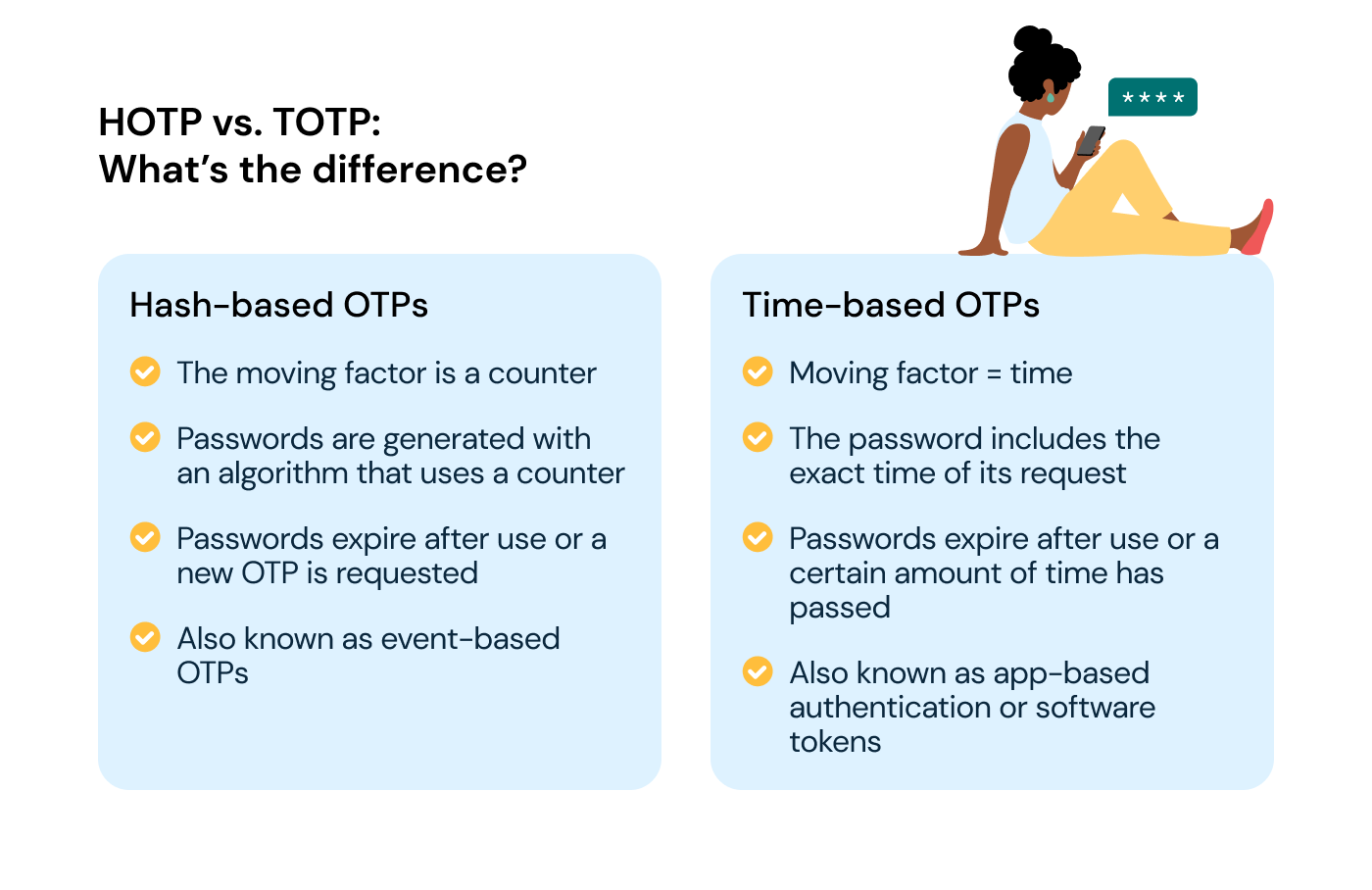
HOTP vs. TOTP
The main difference between a hash-based OTP (HOTP) and time-based one-time password (TOTP) is the moving factor that changes each time the algorithm generates the code.
Hash-based OTPs:
- The moving factor is a counter, which is generated based on the total number of OTPs created
- Passwords are generated with an algorithm
- Like taking a ticket in line at the bakery, the number is included in the password
- Passwords expire after use or a new OTP is requested
- Are also known as event-based OTPs
Time-based OTPs:
- The moving factor is time
- The password includes the exact time it’s requested
- For example, 1:05:43 p.m. = 10543
- Passwords expire after use or a certain amount of time has passed
- Are also known as app-based authentication or software tokens
- Are generally understood as being much more secure than HOTPs because they’re only valid for a specific period of time.
Once issued, the OTP generator shares the new code with the backend authentication server.
When the user enters their code, the OTP authentication server uses the same algorithm as the generator to match the code for easy and instant validation!
Are one-time passwords secure?
Passwords are a weak form of identity verification – 68% of business data breaches in 2024 have involved human error.
So, how can businesses help their customers protect their passwords? Educating them on best practices, like never sharing passwords or reusing them across accounts, helps. But for businesses handling sensitive data, that’s not enough. Adding another authentication method like one-time passwords or two-factor authentication boosts security by changing the verification with every login session or transaction.
Still, OTPs can be vulnerable to hackers. That’s why we recommend SIM-based verification methods which require users to interact with a prompt on their mobile devices, making life hard for opportunistic hackers.
What are the benefits of OTPs?
OTPs are highly versatile, leveraging the widespread use of mobile devices to reach users across the globe. They can be delivered through different channels, making them accessible and user-friendly.
With OTPs, organizations can offer their users a secure, scalable, and hassle-free authentication experience, safeguarding sensitive information and instilling trust in their digital platforms.
The core benefits boil down to:
- Enhanced fraud and data protection
- Scalable global reach on mobile devices
- Convenience and ease of use
Each benefit deserves some special attention, so let’s dive in.
Stop identity thieves in their tracks
Businesses using OTPs make it much harder for unauthorized access to customer or employee accounts.
As a demonstration, let’s think about what might happen when an unauthorized person attempts to access another’s online account. The rightful user receives a code they didn’t request – definitely a red flag. While the business might not know if the attempt was legitimate, the user quickly realizes something’s off and updates their password.
Verification messages are also sent if an unrecognized device tries to access the account, so the user can flag suspicious activity easily. This way, the user stays in control without unnecessary account lockouts, and businesses show they’re actively protecting personal information, which goes a long way to earn trust!
Highly improbable for others to guess
For such a simple idea (four to eight random numbers), OTPs are remarkably effective at mitigating the risks that come from weak password security.
Let’s look at this mathematically. If you issue a random six-digit code, an identity thief has to guess each number correctly within a short expiration window.
That means 10 possibilities (zero through nine), six times (10x10x10x10x10x10).
In other words, an identity thief has a one in a million chance of getting your OTP right, or a 0.000001% probability.
That’s just for your standard six-digit OTP. If they include eight digits, the would-be identity thief would probably have a better chance of winning the lottery.
Easy to implement across multiple channels
SMS messaging is a popular choice for sending OTPs because it’s fast, reliable, and widely used. In many markets, SMS verification is a budget-friendly option for businesses getting started with OTPs.
But the beauty of OTPs is that they’re versatile, and you can send them through any channel that your customers prefer, like WhatsApp, Rich Communication Services (RCS), email, and more.
Channels like RCS and WhatsApp are especially effective for OTPs because they allow your brand’s messages to come from verified profiles straight to your customers’ inboxes. This added layer of trust reduces the risk of fraud like smishing, ensuring your customers can spot real messages from your business at a glance.
Gives your IT support a break
We’ve all got dozens of passwords and usernames to remember. Who hasn’t forgotten at least one? From the streaming service account to online newspaper subscriptions, it’s no small task keeping track of all that info.
It’s human to be forgetful. Without alternative verification methods, IT staff or customer care will get called in to help people regain access to their accounts, and that time adds up fast.
OTPs can instead be used to reset passwords and save countless hours of manpower. As a result:
- IT and customer support teams have more time to focus their efforts on more productive tasks and business-critical issues.
- The user has a quicker and more convenient method of resetting their password and regaining access to their account.
Easy for organizations to integrate and scale
Using verification APIs, organizations can easily build OTPs into their apps and products.
In just a short amount of time, these programmable verification integrations can quite literally pay for themselves by:
- Safeguarding against internal and external cybersecurity threats by militating risk factors for unauthorized internal access, or external threats due to bad actors trying to obtain or guess a user’s regular login credentials.
- Securing customer trust by adding an extra layer of security beyond traditional username and password credentials, assuring customers that their data is safe from unauthorized access.
- Freeing up your valuable human support resources by reducing the need for manual verification and assistance so they can focus on higher-level goals.
Improves the user experience
According to our 2024 research, 61% of consumers expect 2FA messages in a minute or less. That means fast, reliable verification is essential for a great user experience. A seamless, speedy 2FA process can make all the difference in how customers perceive your brand’s reliability and security.
Multi-factor authentication solutions like Sinch’s SMS Verification API provide security at scale and a buttery-smooth UX.
With Sinch, one simple integration makes user verification quick and easy through their mobile device, because:
- Everyone has SMS on their mobile phones.
- It’s a familiar and comfortable communication channel.
- People can receive texts almost anywhere in the world for next to nothing.
Endless OTP use cases and examples
Okay, not exactly endless, but pretty close. With verification more critical than ever, more and more industries are turning to two-factor authentication and OTPs to verify user identities. Here are some key sectors making great use of it:
- Financial services and digital banking: OTPs ensure secure login and transaction verification, protecting users’ credit card information, funds, and sensitive data.
- Retail and e-commerce: OTPs validate customer identities during payment processes and confirm transactions, helping to prevent fraud.
- Healthcare: OTPs ensure secure access to patient records and confidential information.
- Insurance and employee benefit providers: Insurers can use OTPs to validate and verify claim submissions and access to other important documents.
- IT services: OTPs add extra security for user authentication when employees log in to systems, networks, or applications.
- Business administration: OTPs can secure access to confidential documents, or in workflows that include approval processes.
- Government services: OTPs provide extra security for logging in to portals or applications like tax filing, permit applications, or benefits enrollment.
Across industries, some additional useful applications of one-time passcodes include validating users when they take certain actions, like:
- Authenticating their identity
- Authenticating a device
- Registering as a new user
- Signing in and logging on
- Confirming a transaction
- Registering or resetting a password
- Validating a money transfer request
The future of OTPs and authentication
When we think about OTPs of the future, it’s clear the market will keep evolving – both in terms of stronger solutions and increasingly clever cyber threats. So, how can OTPs and authentication stay ahead of the curve? Here are a few key trends shaping the future:
- A more identity-aware internet: Users will increasingly have more control over and interest in their personal data and will demand having safer digital identities.
- Decline of traditional MFA: Stronger customer authentication methods are replacing traditional MFA, thanks to sectors like banking and e-commerce seeking enhanced security and convenience.
- Blending the old and the new: The future will see a mix of traditional verification methods paired with new tech to maintain continuity while boosting security.
- Expanding channels: Mobile-first solutions will grow, with options like Flash Call, Data Verification, and Phone Call Verification becoming key for secure, flexible authentication.
OTPs will no doubt continue to be a part of this landscape, but the future will lie in solutions that continually adapt to changing user preferences and needs.
Learn more about one-time passwords (OTPs) and user authentication
So, there you have it. Now you’ve seen how versatile OTPs can be, and learned how they can help you keep your customers safe.
Want to learn more? Check out these resources to level-up your authentication and verification knowledge in an evolving cybersecurity landscape:
- 5 key takeaways on digital identity and authentication
- How to use machine learning for fraud detection
- What is SMS spoofing and how to prevent it
- Why you should blend verification methods for your mobile app or website
For those really looking to nerd-out, check out our whitepaper on Two-factor authentication.
Otherwise, contact us anytime to chat with one of our experts about how to protect your customers and open the door to better customer engagement!