The digital interactions such as logins, signups, and sensitive online transactions that make life so much easier come with a duty to protect from risks, and criminal exploitation.
Addressing these risks is a complex problem, one that can only be managed by balancing vulnerability, cost, and usability solutions alongside a program of continuous improvement.
So what’s the best way to keep your end-users safe online? The go-to device of today, their very own mobile phone!
How does SIM-based verification help reduce the risk?
Global consumer preferences for mobile devices are widely reported. Even in remote areas, many adults use mobile devices to keep in touch with the world. Sinch’s research indicates that younger consumers are gearing up to adopt mobile messaging-based features for more essential life functions, including online purchases.
The SIM card in any phone is unique. It represents an individual’s telephone number and can be used to verify possession of that mobile phone number. For all but the most sensitive applications, SIM cards are widely considered trusted and secure.
Thanks to SIM security, and the ever-increasing use of mobile devices, SIM-based verification solutions play a significant role in keeping everyone safe online.
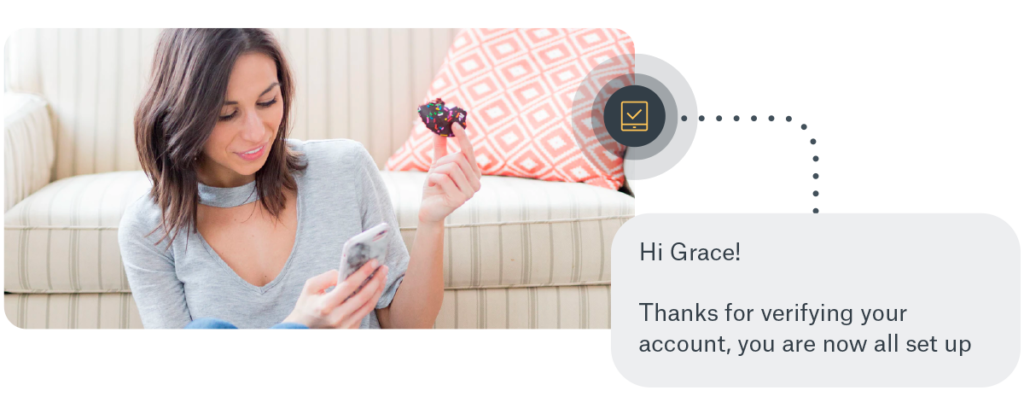
What are the benefits of SIM-based verification?
- Difficult for identity thieves to disrupt, intercept, or emulate SIM cards
Despite what some headlines claim, exploiting mobile operator vulnerabilities at scale is not easy. For most use-cases, SIM-based verification offers the best balance of usability, cost, and risk.
- Can’t be confused or forgotten
With SIM-based verification, each user has only a single identity — his or her SIM-based identity. Users only need to keep their mobile devices secure rather than memorize and frequently update multiple passwords.
- Remains consistent regardless of geography
SIM-based verification methods are available in any country. This, coupled with high mobile phone penetration, makes improving security via one simple method a breeze.
- Suits many use case requirements
SIM-based verification falls into three categories: SMS, voice, and data. These methods are used to onboard and authenticate new users to authorized services or add a second factor of authentication (2FA) onto existing identity solutions. Whether interacting with users directly or indirectly, all types of verification have a role to play.
Identity and access management is a huge topic. Enterprises, large and small, recognize the need to provide rich, secure digital experiences to their customers, while reducing friction and keeping revenue on their platform/in-app.

SIM-based verification ticks all these boxes:
- Stronger account security
- Simpler sign up
- More seamless user experience
- Improvements to business-critical KPIs (e.g., conversions, retention, and loyalty)
- Keep your independence
- Known around the world
- Support for a wide range of use cases
Modern SIM-based verification methods are more than tools — they represent an exciting field for global application developers looking for solutions to quickly and safely authenticate end-users without third parties. Now is the time to lay the foundation for a problem-free identity verification future.
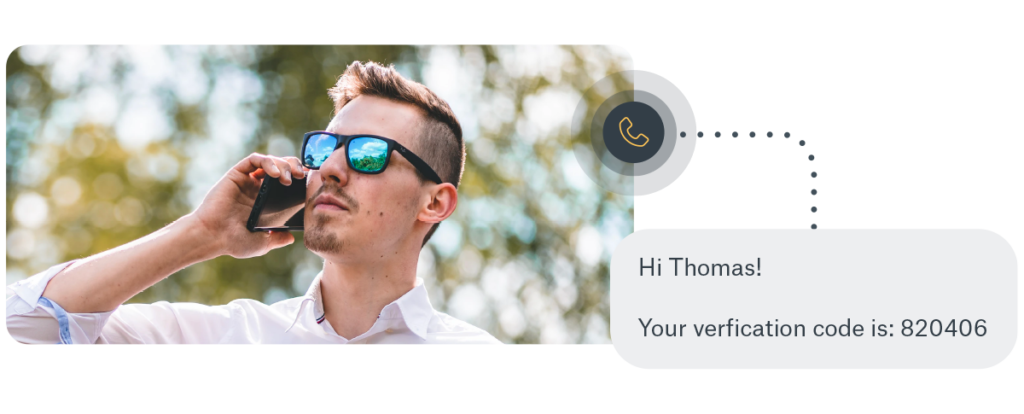
Get started with SIM-based identity verification from Sinch
Sinch provides a variety of SIM-based identity verification methods. Our partners enjoy a one-stop-shop thanks to our portfolio of capabilities, which they can mix and match according to their needs. Get a quick preview of each of Sinch's verification capabilities and how they work: SMS Verification, Phone Call Verification, Data Verification, and Flash Call Verification.
Sign up using our self-service portal to start testing in minutes.



