Products
Verification solutions: Understanding the options

IT leaders, it’s time to elevate enterprise security and streamline operations. With cyber threats increasing, boosting defenses with top-notch verification solutions is crucial.
Verification is how you verify a user. In other words, confirm they are who they are they are. It’s a vital step in protecting sensitive data and preventing fraud.
In this blog post, we’ll explore some of the most effective verification methods – how they can strengthen enterprise security and keep data breaches at bay.
Phone call verification
Phone call verification is a popular way to confirm ID. It works by sending a code to the user’s phone, which they enter to access an account or service.
This process is known as two-factor authentication or 2FA. It’s an effective way to stop unauthorized access and protect sensitive data. The financial services and healthcare industries often use phone call verification to protect sensitive information.
While phone call verification is an effective way to confirm ID, there are cons to consider. What if a phone number is being compromised or a user can’t access their phone?
Learn more about Phone Call Verification, or watch our video to see how voice codes enable verification in more than 200 territories worldwide.
SMS verification
Another popular verification method is SMS verification. This process sends a one-time passcode (OTP) to the user’s cell phone vis SMS. The user then enters the code to access an account or service.
SMS verification is an effective way to prevent fraud, but like phone verification, there are some potential drawbacks – compromised or out-of-date phone numbers.
Learn more about SMS identity verification, then watch our video to see how sending SMS identity verification reaches customers worldwide and builds trust.
Data verification
The new authentication method removes the social engineering risk associated with OTPs. It’s also super-quick and needs no user interaction!
So how does it work? Easy – it compares the end user’s phone number against a carrier-issued token representing the end user’s mobile data session safely and automatically, with errors minimized.
Robert Gerstmann, co-founder and Chief Evangelist at Sinch, explains how data verification works, and how it compares to OTPs when it comes to user experience and conversion rates.
Learn more about Data Verification, and watch our video to see how it works!
Flash calling verification
With flash calling, the user receives a call to their mobile. The phone number used to make this automated call is selected randomly from a large pool of in-service numbers. The number called from acts as a one-time code. The mobile app intercepts the call and automatically sends a request to validate that the calling party number matches the verification request. The result? Quick and easy verification with no end-user action needed.
This method is widely used in e-commerce and banking, where real-time authentication is required. Flash calling is an effective way to prevent fraud, but there are considerations. Voice recognition could be compromised, or a user might not have their mobile phone to hand.
Learn more about Flash Call identity verification, and watch our video about how they work!
Choosing the right verification enterprise solution
It’s critical to consider:
- Security needs
- User experience
- Use case
Evaluate the different types of verification solutions and compare the benefits and drawbacks. As an IT leader, work with your team to choose the best solution for your enterprise.
Lee Suker, identity verification expert and Head of Authentication at Sinch, in a Spiceworks.com, says that “the fact is; companies need to assess the full range of authentication techniques and choose the most appropriate method for their use case: account sign-ups, transaction approvals, logins, etc. And it should be easy for them to do so. Now that communications channels have moved to the cloud, providers such as Sinch will offer a single unified API to cover all the techniques. After all, it’s not just consumers that need a good UX .”
Verification solutions are essential for modern enterprises looking to boost security and protect sensitive data. There are several verification solutions available, each with its benefits and drawbacks. Phone call and SMS verification are popular methods for confirming a user’s identity, while data and flash calling verification are more suited to ensuring real-time authentication.
Magnus Lundstedt, Product Manager for Verification at Sinch, explains the differences between four verification methods: phone call, data, SMS, and flash call.
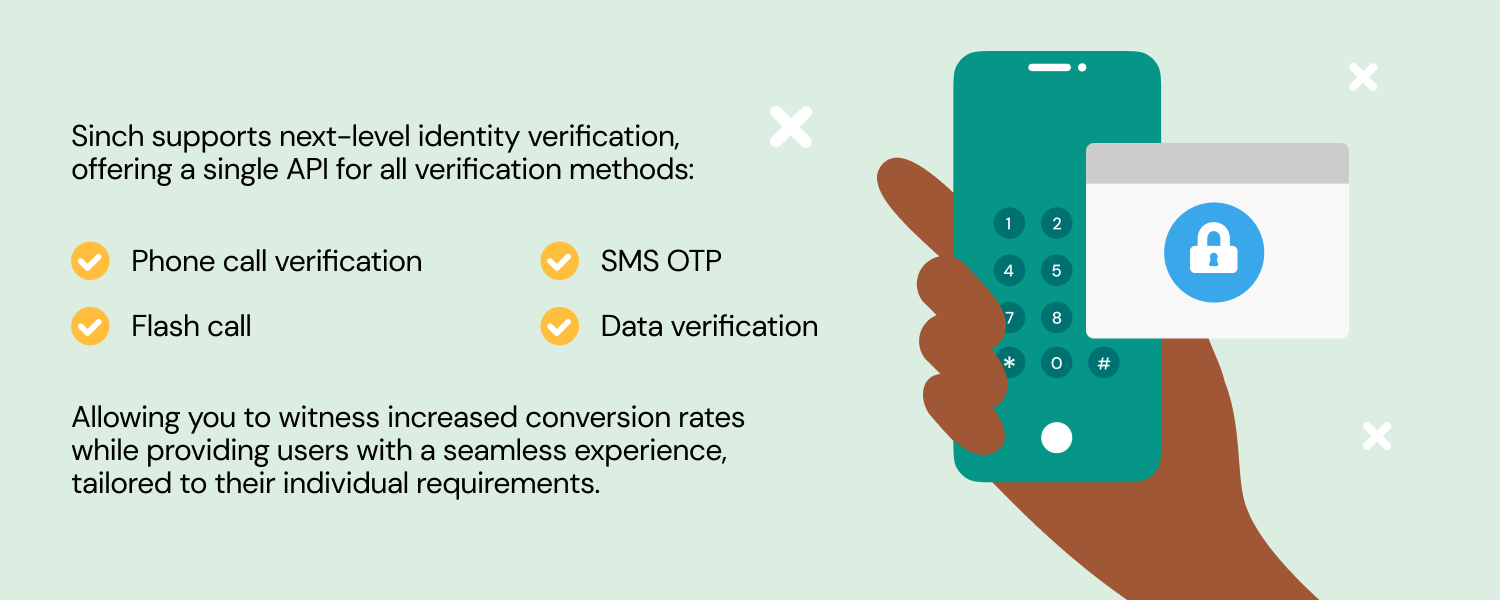
Sinch API supports next-level identity verification
At Sinch we’re super proud of our single Verification API – our deep understanding of identity verification and best practices at your disposal to help streamline customer onboarding and simply login and approvals.
Learn more about Sinch Verification and talk to an expert about the next steps.