Products
SMS and its need for speed

Let’s be clear, we’re not talking about how long it takes for a message to leave your phone and arrive on your friends (although we know this is extremely important), we are talking about SMS service with relation to enterprise to consumer messaging, e.g. when your bank sends you a fraud notification.
Message delivery time is critical
The industry divides enterprise to consumer messaging into two types of messages – transactional and promotional. There is an implied speed for each type, for transactional messages delivery needs to be fast, for promotional messaging it’s not necessary for it to be quite so quick.
Transactional messages
- Financial balance alerts, hotel booking confirmations, one time passwords etc. – a one-time message usually opted in to and sent on an as needed basis. In some cases the messages are sent whilst the user is in session, e.g. on the web making a booking. Transactional messages are expected to be delivered within minutes
Promotional messages
- Vouchers, redemption codes, special offers etc. – usually opted in to on a ‘per brand’ basis and will be sent until the user opts out. These types of messages are not as time critical as transactional messages and are expected to be delivered within 1 hour of being sent
By far the most important transactional messages are those sending a PIN code or password required to transition to the next step in a process, e.g. logging in to access an online account or resetting a password. For the sake of clarity, we will group this subset of transactional messages into one and call them “two factor authentication” (2FA) messages.
Message latency and its affect on conversion
It should be noted that the speed to deliver a message, or the delivery time, is often referred to as the latency of a message. The true meaning of latency can require a magnifying glass in some contracts, because the definition can vary significantly from one provider to another, and in most cases does not actually mean the time from when a user requests the message to when they receive it on their phone.
Our starting point in answering the question, “Just how important is the delivery time of an SMS message?”, was to look at other digital communications and see if there were any similarities. We started with looking at web page loading times and associated drop off of conversion.
We found this excellent infographic on the importance web page load time has on conversion. Kissmetrics found that 35% of surveyed users would abandon a page within 10 seconds of waiting. Intuitively, this sounded roughly about what most users would do if they did not receive a 2FA message within the same time period, but we needed proof.
Many companies who implement 2FA have this data at their fingertips, but because CLX only carries 2FA messages, and is unable to know exactly when a user actually enters the code, we needed some other mechanism to determine the tipping point, the point when the user becomes impatient and requests another message. After racking our brains we realised the most likely thing someone would do if the 2FA message was delayed would be to do exactly that – request another one!
We embarked on a journey of discovery to determine what the ‘repeat request’ rate was as a function of delivery time. As 90% of CLX messages are delivered in less than 5 seconds, we needed to seek out periods where we had rare, but known blips of congestion either due to a carrier network being down or other issue.
When using 2FA, the need for immediate delivery of the text message to the handset is not only required, but expected by the consumer. But how “immediate” does the message have to be? How long are people willing to wait to receive the text before making an additional request to resend the message?
To determine this threshold, we specifically looked at one-time-request versus multiple-requests-per-unique-mobile-number. Prior to analysis the data was cleansed, i.e. for non-delivery issues we did an HLR on all handsets in the data set, and excluded those that showed any kind of potential delivery issue. We then deleted repeat requests from non-existent numbers, as this would indicate someone had entered their mobile number incorrectly.
The first finding from our analysis showed multiple requests to be infrequent, in fact 98% were single entries, meaning the security code was sent to the handset once, the remaining 2% made more than one request. This low percentage for total retries can be explained by the fact that congestion on the CLX network is rare and transient. It is our assumption that every 2FA message will get a repeat request if the message is not delivered within a reasonable and expected period of time.
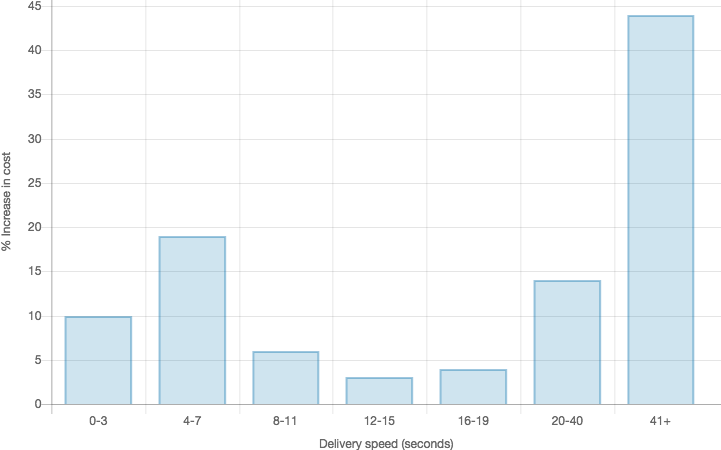
Looking at this data more closely, we can see just how important delivery latency is. First off, 10% of users asked for a repeat message if they did not receive the message within 3 seconds, a further 19% asked for a repeat message if they didn’t receive the message within 7 seconds, and 6% asked for a repeat message within 11 seconds. In total, this is a staggering 35% of users who will ask for a repeat message if the first one is not delivered within 11 seconds. This is very similar to the Kissmetrics finding, showing that 35% of users would abandon a web page within 10 seconds of waiting. We also noted that the average number of repeat requests was 1.2 across the data set, which means for these users, the enterprise will be paying at least double, if not more than double, per user than required – this can be directly attributed to latency.
We conclude that a 2FA message must be delivered within 10 seconds maximum, ideally it should be in less than 3 seconds. There are a number of issues that can impact speed of delivery:
- The rate at which your SMS provider can accept messages needs to be sufficient to ensure that even at peak periods they are able to accept the message within 100 ms
- The capacity your SMS provider has for both delivering messages and doing a mobile number portability lookup (MNP), both are of equal importance
- The ability your messaging provider has to split between low latency and high latency traffic, i.e., split and prioritize messages by whether they are transactional or promotional
- The routing algorithm your messaging provider uses. Some least cost providers will queue messages to send them down the lowest cost route regardless of congestion or latency
- Multi-hop connections make it very difficult to control latency, therefore using direct connections will always lead to higher performance and visibility. Grey routes, SIM farms or other routes that are likely to be blocked can also lead to latency issues as various filters may impact delivery
- Operator SMSC configuration, ideally operators should split A2P and P2P messaging, so retry algorithms within the SMSC can be more aggressive
- Backup connectivity in the event of a primary route failure or direct connection failure is critical. Using SS7 connectivity (albeit at a much higher price) can be beneficial
Recommendations for optimizing speed of message delivery
- Ensure your messaging provider is able to offer an SLA and provide regular reports against those SLA’s
- Choose a messaging provider who has direct connections and SS7 backups to the destinations you are sending to, as this will provide the highest reliability and speed
- Ensure your messaging provider is continuously analysing and monitoring message delivery latency end to end, i.e., to the handset, to ensure problems within carrier networks can be proactively detected
- Ensure your messaging provider can split traffic by message priority at the message provider level, and can send high priority messages out before lower priority messages to the carrier networks if capacity / congestion is detected
- Ensure your application only allows a repeat request after 10 seconds, this will deter some users from being overly trigger happy
CLX has over 100 direct connections worldwide. We proactively monitor our system performance and message delivery times. As part of our monitoring process, our system continually runs tests, some of which are outbound to the carrier networks and partners to measure message delivery times and to alert us to any changes in latency. Early detection allows us to notify and expedite working with carriers and partners to correct the performance.
If you have mission-critical messages and time-sensitive use cases, you need to take message delivery latency seriously, and choose your provider wisely, as the need for speed is real. It seems end user’s patience (or in this case impatience) is universal across multiple channels. Delivery immediacy is a major strength of SMS messaging, and not taking advantage of it could cost you dear in the long run.
First published by CLX Communications.