Operators
A growing menace: flubots, phishing, and network failures

Operators

As we buy more and more stuff online, text messages like “track your order at this link: https://….” are accepted as the norm. You’ve probably clicked one or two of those links yourself, right? And why shouldn’t you?
It sounds innocent enough, but it might not be. That simple SMS could be the vehicle for a flubot attack. Clicking on the link could cause massive headaches for mobile operators and the industry as a whole. Increases in mobile malware pose a real threat to the telecommunications infrastructure. The implications are serious – both operationally and commercially.
Flubots are a sophisticated type of mobile malware that you definitely don’t want to deal with. Successful flubots can cripple telecoms networks by generating huge volumes of voice calls and SMS messages, as well as mobile data traffic targeted at specific websites and servers – also known as a DDOS (distributed denial-of-service) attack.
Flubots work like this: distribution systems send personalized SMS messages containing links that look real, making them difficult to detect and prevent. When a user clicks on the link they are taken to a webpage and prompted to click, triggering a malware download which can then take over the device. Next the software sends a similar message to contacts, while also beginning DDOS attacks. And if that’s not bad enough, the malware can also start phishing for bank details, perform identity theft, or make purchases.
Though you may not be aware of it, flubot attacks are happening – a lot. In October 21 alone, Sinch’s anti-spam platform detected and blocked more than 1.6 million malicious URLs, while one mobile operator recently reported that 10,000 customers had been infected by flubot malware. That attack generated 3,000 messages (both national and international) per customer per day, causing SMS traffic between network operators to soar. In another attack, 5,000 infected devices called a target number every 10 minutes – resulting in about 30,000 calls per hour!
In the graphic below, you can see the evolution of a flubot attack on a medium-sized MNO in the Asia-Pacific region. Our anti-fraud systems captured over 100K fraudulent SMS messages before customers realized anything had happened. And this is just one example…but there were many similar attacks around the same time.
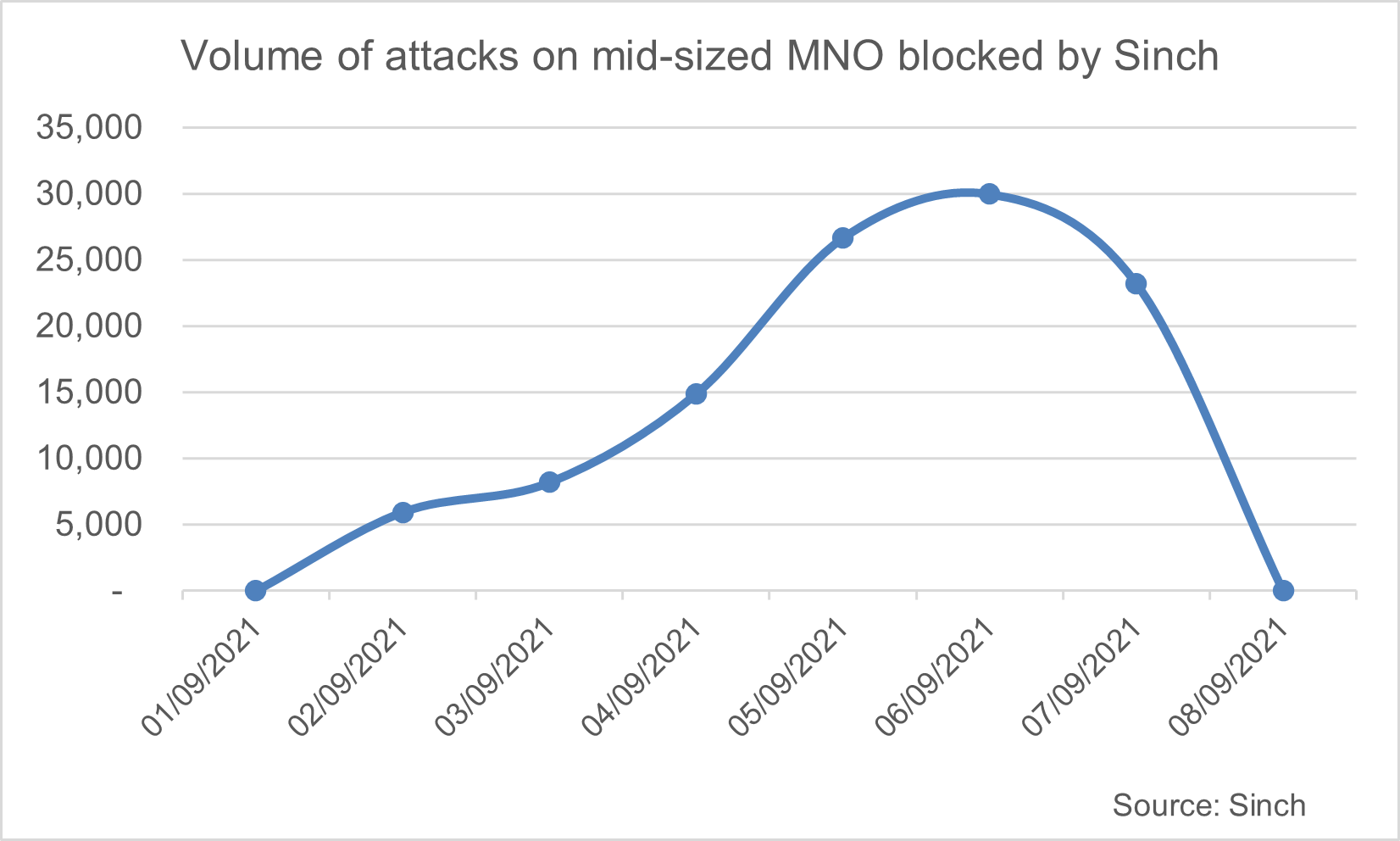
The attack began with an SMS notification for a package delivery. Pretty normal stuff. But the content changed as the attack gained ground. Typically, those who start a flubot attack will change the content of the messages and even intentionally misspell words to sneak through filters and avoid detection.
In some cases, the messages claim to include links to photos sent by friends, vaccine appointments, and even COVID-19 test results. At the height of the attack, Sinch blocked up to 30,000 flubot attacks a day on the APAC operator’s network.
When an attack succeeds, interconnection gateways can quickly become overloaded, and parts of the operator’s core network can be overwhelmed. Regular traffic is displaced, calls can’t get through, messages go undelivered, and customer support costs (in both FTE’s and device repairs) spiral out of control. In addition, impacted subscribers use social media to air complaints which is bad news for the operator’s brand.
For individual consumers, a flubot attack can mean privacy invasions. The malware could hack into the phone’s camera, track its location, record phone calls, access personal data, monitor internet usage, and even use one-time passwords to open bank accounts and online payment services (including direct carrier billing).
Once it has taken over the phone, the malware could click on advertising banners to boost revenue for a specific publisher, use the phone’s computing power and energy for crypto-mining, or use any app on the phone – camera, audio, and social media included. We’re talking major consequences here.
So why has there been a wave of flubot attacks recently? The main reason is data breaches at leading social networks, such as Facebook and LinkedIn. Some 533 million Facebook user phone numbers and personal data were leaked online. The data belongs to people across 106 countries, including over 32 million records on users in the U.S., 11 million users in the UK, and 6 million users in India. Leaked records included their phone numbers, Facebook IDs, full names, locations, birthdates, bios, and, in some cases, email addresses.
Some 500 million LinkedIn users have also been the victims of a data breach, exposing LinkedIn IDs, full names, email addresses, phone numbers, and genders. Of course, it isn’t just these Facebook and LinkedIn users that are vulnerable. When a flubot successfully attacks a phone, it can then steal data from the address books of infected devices, to continue spreading malware.
Governments around the world have started warning consumers about the threat of flubots. But telecoms operators also need to boost their defences to put a stop to these attacks.
So, what can you do? In our next blog post we’ll outline the best measures operators can take to counter the flubot menace – check it out now!
Find out how SMS Transformation can help in the fight against flubots and discover how reliable and safe SMS can be when it’s done right!