Operators
Global title faking in SMS: How to fight back
Operators

Global title faking in SMS is still a massive headache for mobile network operators (MNOs). Our last blog explained how this kind of international revenue share fraud costs large MNOs millions of dollars each month.
How can MNOs stop these losses? Don’t worry. There are ways to disrupt SMS faking, and we’ll get into them in this blog post. The first step is to look at how this kind of fraud works. Join us as we get technical on the details and highlight possible solutions!
SMS faking takes advantage of the multiple steps needed to send an SMS:
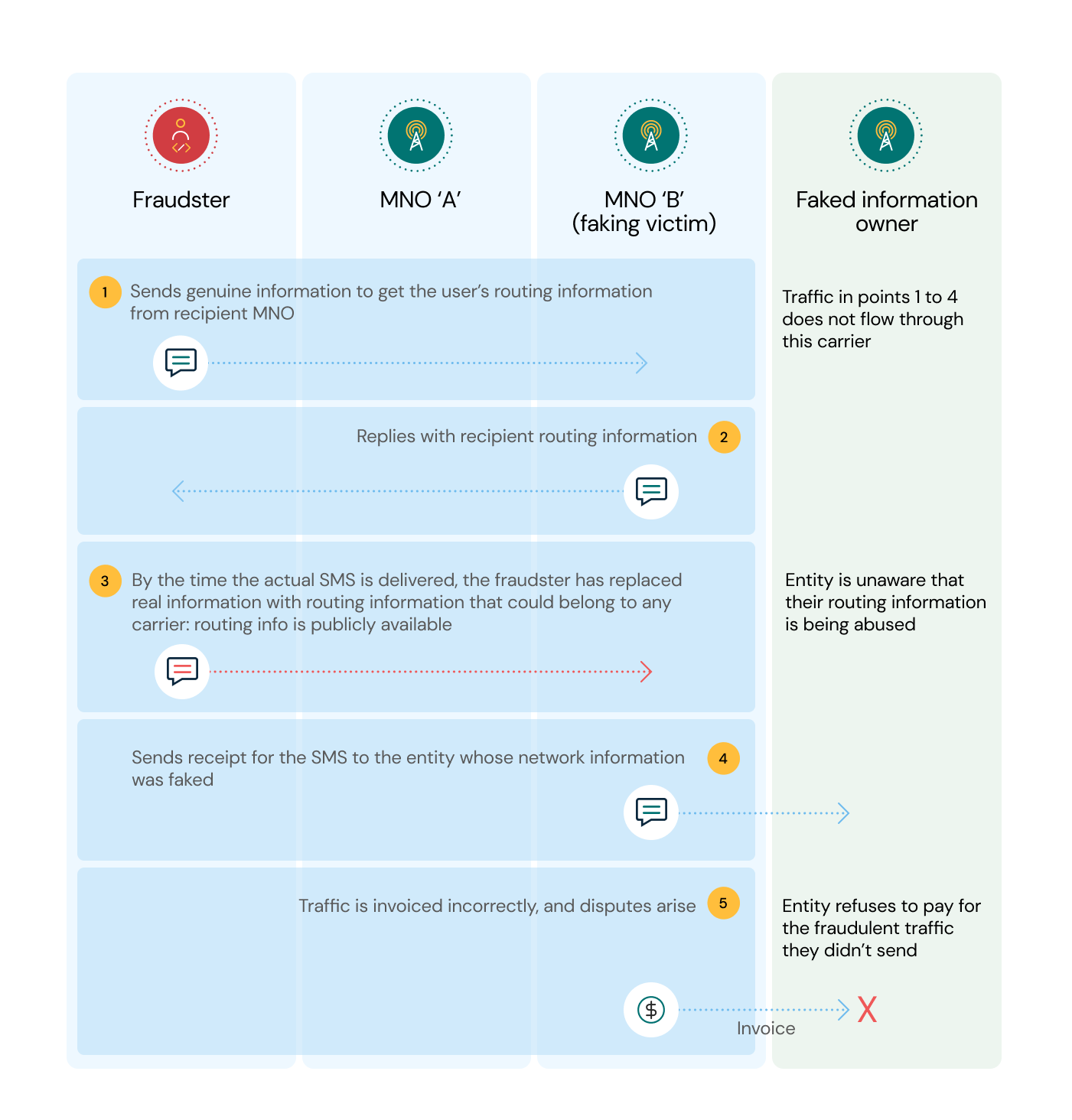
On the first leg (known as the SRI_SM), fraudsters use the international C7 network to send a message to the victim MNO’s home location register (HLR) asking: Does this MSISDN (the mobile number) exist and, if so, is it your customer? During this leg, the originator must include their actual sending address to get the information needed. This real sender address is held in the SCCP layer of the SRI_SM.
On the second leg, the recipient MNO replies, flagging where the customer is so the message can be routed correctly.
On the third leg (the Forward_SM), the fraudster replaces their sending address with a faked or third party’s address. Now it looks like the SMS is sent from someone else via a different carrier.
Because SMS is billed on this third leg and their actual address isn’t attached to the SMS anymore, the fraudster avoids paying for the traffic and gets a third party to pick up the tab.
Let’s assume the fraudster uses an unsuspecting MNO’s sender address: The MNO terminating the SMS will then invoice an MNO who had no part in delivering that SMS. The innocent MNO then refuses to pay the bill leaving the MNO terminating the SMS with the check.
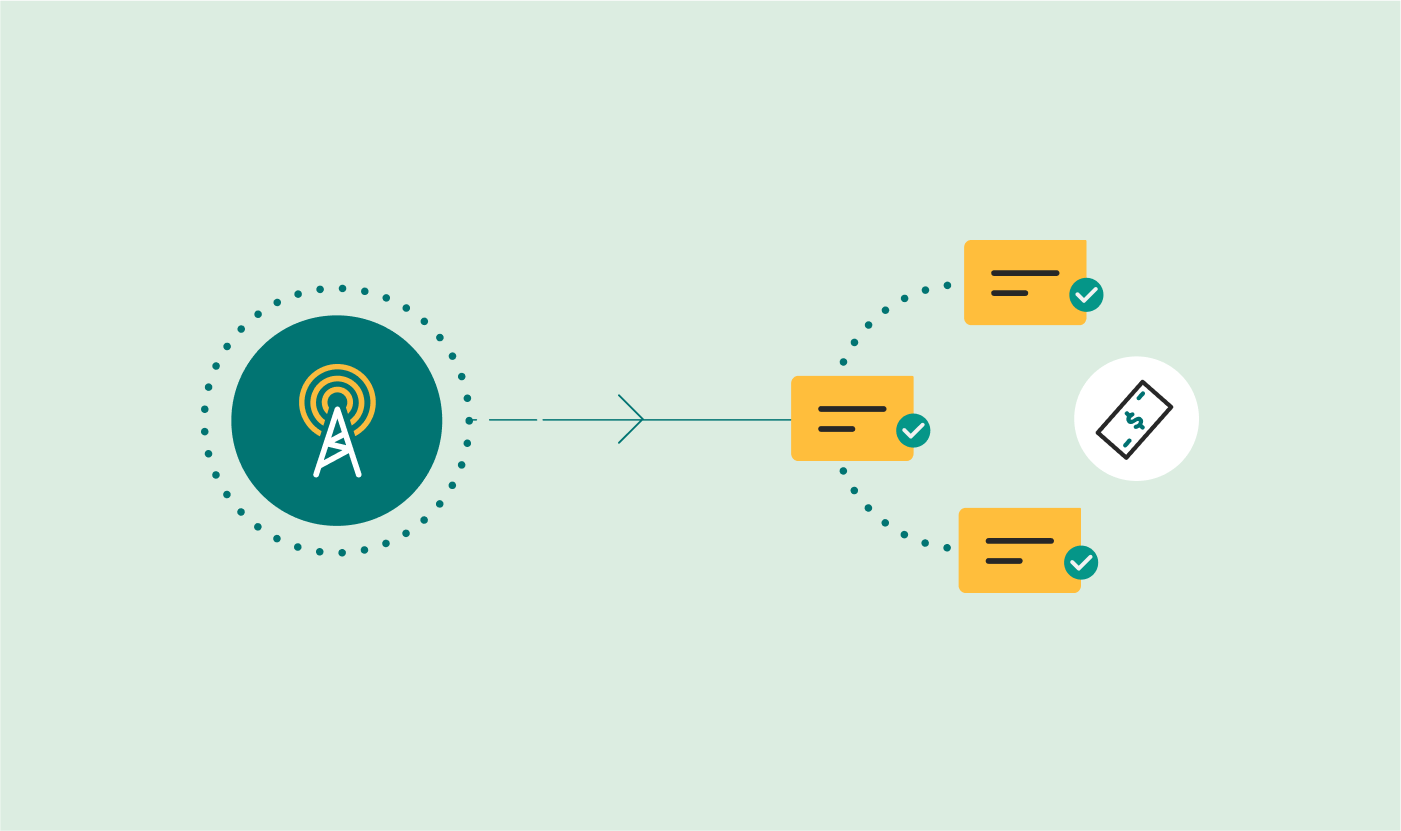
The most efficient (and popular) way to spot SMS faking is to monitor incoming SMS traffic patterns and routes, then investigate any suspicious activity. For example, a spike in the number of SRI_SM received from a specific origin could point to a faking attack.
Operators should compare the number of SRI_SM messages received with the number of Forward_SM messages received from each SMS center or network. The ratio shouldn’t be more than 2.5 SRI_SM for every Forward_SM. If it is, this could mean the SMS center or network is being used for SMS faking.
On the other hand, if there are far fewer SRI_SM messages than Forward_SM messages, it could point to the network or center being manipulated by a fraudster to hide where the SMS traffic began.
If an MNO finds a suspicious pattern, they’ll need to manually check if the sender address information in the SCCP layer of the SRI_SM matches what’s in the related Forward_SM.
If there are differences, the MNO should block the Forward_SM associated with the suspect SRI_SM and urgently contact the actual SMS originator to investigate the address held in the SRI_SM and identify the fraudster.
Other parties in the chain won’t know about the fraud until they get a massive bill. So it’s up to the recipient MNO terminating the fake traffic to step in.
Spotting SMS faking and dealing with it takes a long time and uses precious resources. In fact, the GSM Association offers more than 10 recommendations in its “SMS SS7 Fraud Prevention” guide.
Unfortunately, even today, many MNOs don’t have an automated solution to deal with SMS faking. Because it comes to light after an invoice is generated, it’s almost impossible to find the culprit – traces often disappear after a few days or weeks because of data retention policies.
Luckily MNOs can rely on vendor solutions to identify and block faking efficiently.
At Sinch, we help combat many types of faking, including global title faking, in real-time with the Sinch SMS Firewall. Our fully-fledged SMS protection software solution helps defend P2P traffic links from a broad range of fraud and spam.
Sinch also helps MNOs tackle global title faking with our Suspect Faking Alerts service. Sinch’s P2P hub monitors Forward_SM responses without associated SRI_SM, and when a spike is detected, we alert the MNOs Network Operation Center so they can investigate, identify, and stop the fraud.
If you’d like to learn more about how networks can be exposed to SMS fraud and how Sinch can help, get in touch to speak to one of our experts.

Author: The Sinch team
When you visit any web site, it may store or retrieve information on your browser, mostly in the form of cookies. This information might be about you, your preferences or your device and is mostly used to make the site work as you expect it to. The information does not usually directly identify you, but it can give you a more personalised web experience. Because we respect your right to privacy, you can choose not to allow some types of cookies. Click on the different category headings to find out more and change our default settings. However, blocking some types of cookies may impact your experience of the site and the services we are able to offer.
Cookie Statement
These cookies are necessary for the website to function and cannot be switched off in our systems. They are usually only set in response to actions made by you which amount to a request for services, such as setting your privacy preferences, logging in or filling in forms. You can set your browser to block or alert you about these cookies, but some parts of the site will not then work. These cookies do not store any personally identifiable information.
Cookie details
| Cookie Subgroup | Cookies | Cookies used |
|---|---|---|
| eu5.mm.sdi.sinch.com | ASP.NET_SessionId | First Party |
| community.sinch.com | AWSALB , LiSESSIONID | First Party |
| appengage.sinch.com | dd_cookie_test_ | First Party |
| tickets.sinch.com | atlassian.xsrf.token , JSESSIONID | First Party |
| cockpit2.sinch.com | SESSION | First Party |
| engage.sinch.com | instapage-variant-xxxxxxxx | First Party |
| dashboard.sinch.com | cookietest | First Party |
| brand.sinch.com | PHPSESSID , AWSALBCORS | First Party |
| sinch.com | __cf_bm , OptanonConsent , TEST_AMCV_COOKIE_WRITE , OptanonAlertBoxClosed , onesaasCookieSettings, QueryString, functional-cookies, performance-cookies, targeting-cookies, social-cookies lastExternalReferrer, lastExternalReferrertime, cookies, receive-cookie-deprecation _gdvisitor, _gd_session, _gcl_au, _fbp, _an_uid, _utm_zzses, lpv | First Party |
| mediabrief.com | __cf_bm | Third Party |
| recaptcha.net | _GRECAPTCHA | Third Party |
| cision.com | __cf_bm | Third Party |
| techtarget.com | __cf_bm | Third Party |
These cookies allow us to count visits and traffic sources so we can measure and improve the performance of our site. They help us to know which pages are the most and least popular and see how visitors move around the site. All information these cookies collect is aggregated and therefore anonymous. If you do not allow these cookies we will not know when you have visited our site, and will not be able to monitor its performance.
Cookie details
| Cookie Subgroup | Cookies | Cookies used |
|---|---|---|
| community.sinch.com | ValueSurveyVisitorCount | First Party |
| buzz.sinch.com | instap-spid.8069 , instap-spses.8069 | First Party |
| appengage.sinch.com | _dd_s | First Party |
| sinch.com | AMP_TLDTEST , rl_page_init_referrer , rl_trait , _vis_opt_s , __q_state_dp56h9oqwhna9CoL , cb_user_id , __hstc , rl_anonymous_id , rl_user_id , initialTrafficSource , _vwo_uuid , _vwo_uuid_v2 , rl_page_init_referring_domain , _hjIncludedInSessionSample_xxx , apt.uid , __hssrc , test_rudder_cookie , cb%3Atest , __hssc , rl_group_trait , _hjAbsoluteSessionInProgress , _vwo_referrer , _vwo_sn , _vis_opt_test_cookie , _hjFirstSeen , _hjTLDTest , _hjSession_xxxxxx , s_sq , _vwo_ds , rl_group_id , _vis_opt_exp_n_combi , s_cc , _gclxxxx , cb_anonymous_id , cb_group_id , apt.sid , rl_session , _uetvid , AMP_899c7e29a9 , _hjSessionUser_xxxxxx | First Party |
| brand.sinch.com | AMP_TEST | First Party |
| engage.sinch.com | no-cache , instap-spses.85bb , instap-spid.85bb | First Party |
| www.sinch.com | d-a8e6 , s-9da4 | First Party |
| nr-data.net | JSESSIONID | Third Party |
| sinch-en.newsroom.cision.com | _ga, _gid | Third Party |
| sinch.in | _ga_xxxxxxxxxx, _gat_UA-XXXXXX-X, _gid, _ga | Third Party |
| g.fastcdn.co | instap-spses.85bb | Third Party |
| hello.learn.mailjet.com | pardot, visitor_id, visitor_id##### | Third Party |
| www.googletagmanager.com | userId | Third Party |
| hello.learn.mailgun.com | visitor_id#####, visitor_id | Third Party |
| dev.visualwebsiteoptimizer.com | _vwo_ssm | Third Party |
| box.com | box_visitor_id | Third Party |
| app.box.com | z, cn | Third Party |
| sinch-tfn.paperform.co | laravel_session | Third Party |
| go.sinch.in | visitor_id#####, visitor_id | Third Party |
| Qualified | __q_local_form_debug | Third party |
| Rudderstack | rudder.inProgress, rudder.3156dd1f-7029-4600-ae54-baf147d9af20.queue, rudder.3156dd1f-7029-4600-ae54-baf147d9af20.ack, rudder.3156dd1f-7029-4600-ae54-baf147d9af20.reclaimStart, rudder.3156dd1f-7029-4600-ae54-baf147d9af20.reclaimEnd, | Third party |
| 6sense | _6senseCompanyDetauls, _6signalTTL | Third party |
| Appcues | apc_local_id, apc_user | Third party |
These cookies enable the website to provide enhanced functionality and personalisation. They may be set by us or by third party providers whose services we have added to our pages. If you do not allow these cookies then some or all of these services may not function properly.
Cookie details
| Cookie Subgroup | Cookies | Cookies used |
|---|---|---|
| portal.sinch.com | pnctest | First Party |
| partner.appengage.sinch.com | _dd_s | First Party |
| investors.sinch.com | First Party | |
| community.sinch.com | LithiumUserInfo , LithiumUserSecure | First Party |
| tickets.sinch.com | selectedidp | First Party |
| engage.sinch.com | ln_or | First Party |
| cockpit2.sinch.com | CSRF-TOKEN , NG_TRANSLATE_LANG_KEY | First Party |
| sinch.com | apt.temp-xxxxxxxxxxxxxxxxxx , hubspotutk , ajs%3Acookies , cf_clearance , ajs%3Atest , __tld__ , __q_domainTest , pfjs%3Acookies , ajs_anonymous_id | First Party |
| auth.appengage.sinch.com | AUTH_SESSION_ID , KEYCLOAK_3P_COOKIE , KEYCLOAK_3P_COOKIE_SAMESITE , KC_RESTART , AUTH_SESSION_ID_LEGACY | First Party |
| www.recaptcha.net | _GRECAPTCHA | Third Party |
| boxcdn.net | __cf_bm | Third Party |
| d2oeshgsx64tgz.cloudfront.net | cookietest | Third Party |
| sinch-np.paperform.co | XSRF-TOKEN, laravel_session | Third Party |
| vimeo.com | __cf_bm, vuid | Third Party |
| sinch-ca-sc.paperform.co | XSRF-TOKEN, laravel_session | Third Party |
| box.com | site_preference | Third Party |
| app.box.com | bv | Third Party |
| sinch-tfn.paperform.co | XSRF-TOKEN | Third Party |
| cision.com | cf_clearance | Third Party |
These cookies may be set through our site by our advertising partners. They may be used by those companies to build a profile of your interests and show you relevant adverts on other sites. They do not store directly personal information, but are based on uniquely identifying your browser and internet device. If you do not allow these cookies, you will experience less targeted advertising.
Cookie details
| Cookie Subgroup | Cookies | Cookies used |
|---|---|---|
| investors.sinch.com | visitor_id | First Party |
| community.sinch.com | VISITOR_BEACON , LithiumVisitor | First Party |
| sinch.com | _uetsid , ajs_user_id , _gcl_aw , ajs_group_id , AMCV_ , __utmzzses , _fbp , _gcl_au , AMCVS_ | First Party |
| go.latam.sinch.com | visitor_id##### , pardot | First Party |
| linkedin.com | li_gc, bcookie, lidc, AnalyticsSyncHistory, UserMatchHistory, li_sugr | Third Party |
| pi.pardot.com | lpv151751, pardot | Third Party |
| hsforms.com | _cfuvid | Third Party |
| google.com | CONSENT | Third Party |
| sinch.in | _gclxxxx, _gcl_au | Third Party |
| www.linkedin.com | bscookie | Third Party |
| bing.com | MUID, MSPTC | Third Party |
| www.facebook.com | Third Party | |
| hello.learn.mailgun.com | pardot | Third Party |
| www.youtube.com | TESTCOOKIESENABLED | Third Party |
| dev.visualwebsiteoptimizer.com | uuid | Third Party |
| g2crowd.com | __cf_bm | Third Party |
| pardot.com | visitor_id#####, visitor_id | Third Party |
| tracking.g2crowd.com | _session_id | Third Party |
| hubspot.com | __cf_bm, _cfuvid | Third Party |
| doubleclick.net | test_cookie, IDE | Third Party |
| youtube.com | CONSENT, VISITOR_PRIVACY_METADATA, VISITOR_INFO1_LIVE | Third Party |
| go.sinch.in | pardot | Third Party |
| liadm.com | lidid | Third Party |
| www.google.com | _GRECAPTCHA | Third Party |
These cookies are set by a range of social media services that we have added to the site to enable you to share our content with your friends and networks. They are capable of tracking your browser across other sites and building up a profile of your interests. This may impact the content and messages you see on other websites you visit. If you do not allow these cookies you may not be able to use or see these sharing tools.
Cookie details